Securing Your Privacy in the Digital Age
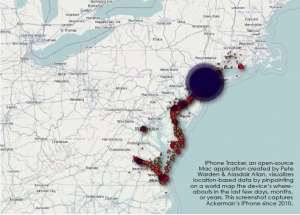
Even when driving alone across a bridge that spans the ocean, surrounded by nothing but salty air and hovering seagulls, a company based out of Cupertino, California may be gathering data about where you are and where you have been.
Apple, maker of the iPhones that many of us tote in our pockets or bags, receives anonymized location-based data from their products every 12 hours, as long as the device has Locations Services enabled and is connected to a wireless network. Increasingly, the gizmos that individuals use on a daily basis are leaving behind data cookie crumbs, leading Internet companies and the government directly back to the source.
Reports by leading news organizations over the last six months have revealed that the data-collecting infrastructure of the U.S. National Security Agency (NSA) reaches deep into the networks that connect our lives. Though domestic surveillance in the United States is not a new issue, recent developments have sparked a widespread debate about data-collecting schemes and the use of privacy-protecting resources.
“We have become used to the convenience of our devices and websites,” said Niko Para and Anne Roth of the Tactical Technology Collective, an international organization that provides information and communication technology resources to advocates, in an email to the *Free Press*. “[We] need to think about who else has access to the information about our lives that we leave as traces on the web.”
Studies show that American interest in online security has increased significantly over the last few years. In 2007, a report produced by the Pew Internet & American Life Project, sponsored by the Pew Research Center, found that 60 percent of Internet users were not concerned about the amount of information that was available about them online. A study by the same group in 2013 concluded that 86 percent of Internet users have taken simple steps to limit their digital footprints, such as encrypting emails, and 55 percent have taken further precautions to avoid surveillance by governments and other organizations.
While some New School students are concerned about their Internet security and privacy, as many as 30 people questioned for this article were not fully aware or distressed about the data trails that their digital activity leaves behind.
This article is meant to be a helpful resource that brings readers up to speed on the recent NSA related revelations and digital tracking, provide expert opinion on the topic, and introduce privacy-protection tools to enhance digital security. However, the guide outlined in this article does not offer full protection from the NSA or other digital eavesdroppers. The ultimate hope of this resource is to establish a dialogue within the New School community about digital literacy and privacy.
On December 5, the New School’s Center for Public Scholarship will host a conversation on surveillance in the United States. Experts will discuss the governmental operations carried out on American citizens in the Tishman Auditorium at 6 p.m.
5 Things You May Have Missed
- What’s the NSA? In 1952, the National Security Agency was created under President Truman to collect and process intelligence. While finding a balance between security and privacy has been a longstanding conflict with the agency, the attacks on September 11, 2001 led the U.S. to substantially increase domestic surveillance to fend off future terror attacks.
-
What was revealed? In June 2013, the Guardian published details from classified documents leaked by former NSA contractor Edward Snowden, exposing the often warrantless mass-surveillance and data collecting programs of the NSA and British Government Communications Headquarters (GCHQ). According to an article released on June 6, an NSA program called PRISM allows the government to obtain, “email, video and voice chat, videos, photos, voice-over-IP (Skype, for example) chats, file transfers, social networking details, and more” from many of the largest Internet service providers. Just a day before, the newspaper revealed that the agency is currently collecting telephone records from millions of American Verizon customers.
- What data trails are left behind? Online service-providing companies such as Facebook and Google collect vast quantities of information about their users, including browsing and search histories, names, locations, email addresses, communications, relationships, IP addresses, among other forms of data. These companies can personalize user experience through targeted advertising and other interest-based tools that utilize data. Many of these service-providing companies are transparent about the data that they collect and offer information outlining what is used, such as Facebook’s “Data Use Policy.”
- Inserting backdoors: In September, the leaked NSA documents from Snowden’s four laptops revealed another groundbreaking discovery — that the NSA and GCHQ have inserted vulnerabilities, also known as trap or backdoors, into commercial encryption and other online security protocols, including the encryption used to protect banking and medical records.
-
What else is happening with the NSA? More recent reports by The Guardian have revealed that 35 world leaders have had their phone calls monitored by the NSA, including German Chancellor Angela Merkel, who accused the US of spying on allies. The Washington Post also published evidence that Internet companies such as Google and Yahoo! have had their data centers’ communication links tapped so that the NSA can collect data from millions of user accounts.
What Experts Say
“It becomes especially important as a young adult in the digital age to realize that even now the record of your online activities are being recorded,” said Para and Roth, of the Tactical Technology Collective, “And that websites you visit and contribute to now will be logged in your future as well.”
Tactical Tech is currently working on an awareness-raising project titled Me & My Shadow. The website, which is still in its beta phase, informs individuals of their online presence by visualizing a ‘digital shadow.’
“So, your political views, where you shop, who you love, where you work and your personal interests could cast you as a particular sort of individual in the eyes of marketers, future employers and the state itself,” they said.
Though many experts believe that privacy-protecting resources are necessary for securing sensitive information, changing habits when using networked devices can be a daunting task.
“There’s a big psychological barrier when it comes to technology that’s ‘different’ from your normal way of doing things, so being exposed to these ideas [of using encryption] and tools helps spread good habits,” said Mike Tigas, ProPublica’s 2013 Knight-Mozilla OpenNews Fellow and developer of the Onion Browser, a Tor-based web browsing application for iOS devices.
“I think everyone understands the idea of having secrets and wanting to say or send something to a friend in private,” he said. “Tools and techniques differ with every situation, but I think understanding basic aspects of the Internet and how to stay safe on the Internet apply to anyone these days.”
While normalizing the use of privacy-protecting resources is one way to limit digital tracing, some advocate for Internet companies to build protection for users into their services.
“If everybody started to use Off-the-Record chat while they were using Facebook chat, then what happens is all the information that Facebook gets is a bunch of encrypted stuff that they don’t know what to do with,” said Micah Lee, a staff technologist for the Electronic Frontier Foundation, a non-profit digital rights organization. “This will be great if everybody does it, but in fact I think this would be great if Facebook enforced this, if Facebook built Off-the-Record into their service so they wouldn’t be able to see what people are saying on it.”
But other experts believe that the NSA’s data-collecting and surveillance programs are necessary to cyber-security and counterterrorism efforts. In an article titled “We Need an Invasive NSA” from the New Republic, Harvard Law School professor Jack Goldsmith argues that the NSA’s activities are of value to the American public.
“As cyber-theft and cyber-attacks continue to spread (and they will), and especially when they result in a catastrophic disaster (like a banking compromise that destroys market confidence, or a successful attack on an electric grid), the public will demand government action to remedy the problem and adjust its tolerance for intrusive government measures,” he wrote.
While safety is a valuable goal, some believe that rights such as privacy and freedom may be undermined by increased surveillance.
“We have an increasingly insecure digital infrastructure and an increasingly important digital infrastructure and I think that’s something that is going to cost us–to aim for greater and greater levels of security and certainty,” said John Palfrey, the head of Phillips Academy, Andover and Director of Harvard’s Berkman Center for Internet & Society. “Oftentimes, that certainty and security translates to something that undercuts other things that we value, which includes freedom and privacy. So I think the challenge is going to be to say, what’s enough security?”
Secure Browsing & Search
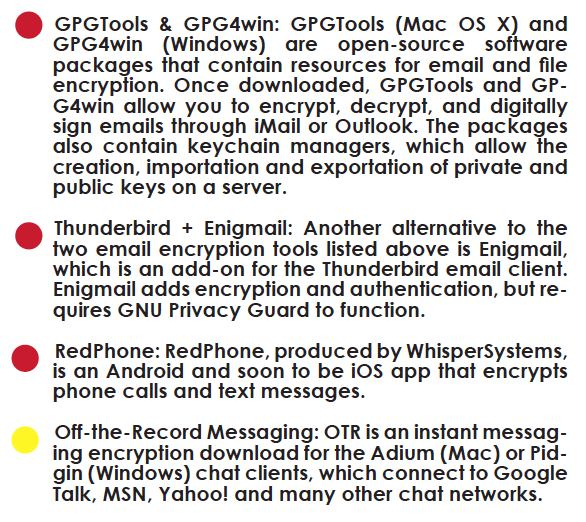
Secure Communication
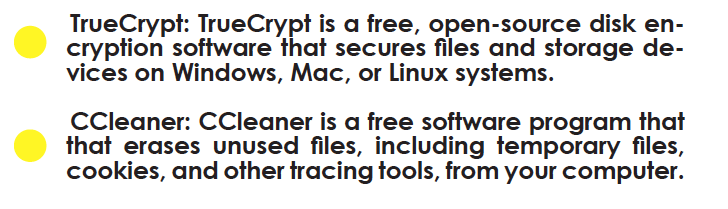
Secure Computer Files
In addition to these resources, another alternative for securing sensitive information is to keep a laptop that has never been connected to the Internet for holding private documents and other materials.
Illustrations by: Daniel Marin
Editor-in-Chief | Alexandra hails from Virginia Beach, VA and is a senior in Culture and Media Studies at Lang, with a minor in Journalism. She is interested in both data journalism and innovations in new media. See what else Alexandra is up to on Twitter!